Messages can infect devices with malware that can do serious damage, but there are red flags that are easy to spot, says a senior advisor for Toronto Metropolitan University’s Rogers Cybersecurity Catalyst.
A new version of a long-running phishing scam is making the rounds in Canada.
Fake copyright and trademark notices
Experts are warning about an international copyright infringement scam that includes a fake PDF attachment, which can infect devices with an information-stealing malware.
Hackers send a notice claiming to be from a law firm with details about a “serious violation” of copyright laws and threaten legal action. The urgent and threatening tone pressures recipients into performing dangerous actions like clicking malicious links to hacker controlled pages or downloading malware-infected attachments.
The malicious software can dodge antivirus scans and inflict serious damage.
Officials see spike in phishing attempts related to intellectual property
The approach isn’t new.
In May, the Canadian Intellectual Property Office (CIPO) posted a warning about a spike in phishing attempts related to intellectual property (IP). Many of the scams involve hackers pretending to be from an attorney, agency or even the CIPO itself, the agency shared.
“Typically sent by email or mail, these communications frequently use official-sounding language, reference public CIPO records, and sometimes even use the words ‘Canada’ or ‘Canadian’ in their branding to appear legitimate,” the agency said, adding these often pressure people to act quickly.
This type of scam has been around for years. Many iterations looking to spread new types of malware or steal login information have popped up in the past, with newer versions emerging every few months.
2025 copyright scam uses spear phishing and fake PDFs to infect devices
The new version exposed by researchers from cybersecurity firm Morphisec uses a highly targeted, advanced spear phishing campaign. Spear phishing is a targeted type of attack that uses publicly available information about the target to make the hook more convincing.
The email for the copyright scam is tailored to the person with precise details about the target, indicating “extensive reconnaissance,” researchers said.
This means planning and information gathering were performed to find details about the recipient before launching the attack.
In a previous interview with Metroland Media, cybersecurity expert John Hewie, who previously worked as a national security officer for Microsoft Canada, said hackers are now using AI to gather background information and scrape publicly available data about a target to make spear phishing attacks more believable.
According to the report, the messages also include fake PDF attachments that hides a dangerous infostealer called Noodlophile. Hackers are using advanced techniques to embed the malicious content making it harder for antivirus scans to detect and filter out the fake notice.
What can a Noodlephile infostealer do to your device?
“Noodlophile Stealer is a type of malware designed to quietly run in the background of an infected computer, where it actively collects sensitive data and makes changes to survive, even after a restart,” said Randy Purse, senior advisor for cybersecurity training and education at Toronto Metropolitan University’s Cybersecure Catalyst.
Using the stolen data, cybercriminals can do serious damage to the individual or their company, Purse warned.
“They may drain bank or crypto accounts, take over email and social media profiles, impersonate you online, or sell your information to other criminals,” Purse explained.
If hackers gain remote access to the victim’s device, they can capture passwords, collect keystrokes, take screenshots or use the device to launch other attacks.
“In short, a single infection can lead to financial theft, identity fraud, and ongoing privacy violations — turning one compromised computer into a gateway for much larger problems,” he explained.
Red flags to help spot copyright infringement scam messages
While cybercriminals are constantly evolving their scams to make them more convincing, the good news is most attacks still rely on one simple action: getting someone to click, Purse said.
Here are some red flags to look out for:
Red flags to help spot copyright infringement scam messages
A screen grab shared by Morphisec shows a generic or free gmail.com domain in the sender’s email address field, as shown below.
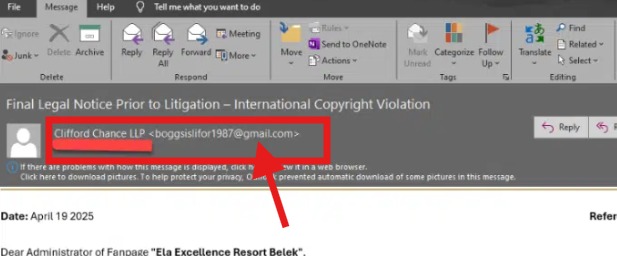
These fake copyright infringement scam emails appear to come from a generic Gmail address, as shown in this screen grab by Morphisec.
Legitimate copyright notices will come from a company or organization’s official domain address. Email notices from the CIPO for instance, will have the @ised-isde.gc.ca domain in the sender’s email address.
Unusual attachment file type
“Many of these scams disguise malware as a ‘PDF’,” Purse said. But once victims download the file, they might notice that the actual download is an installer file with .zip, .rar, or. msi file extension. This is unusual for a file that should just be a document, he said.
Poor formatting or odd phrasing
Some of these emails might not read like a professional message from a legitimate company and recipients can easily spot grammatical errors or weird formatting.
It is important to note, however, that a polished and perfect-looking email does not automatically mean the message is legitimate. Earlier this year, experts warned about scammers using generative AI to craft polished copy for emails in minutes.
Links that don’t match the sender
“Pay attention to where links lead,” Purse advised.
Even if the text says “view PDF,” recipients can hover their mouse over the link (without clicking) to reveal a web address. An address that does not appear to match the supposed sender is a big red flag.
Threatening language and tone
Hackers often use threatening or urgent language like “your account will be deleted” or “legal action will be taken immediately” to push recipients into clicking without thinking.
“Real legal or copyright notices typically don’t come with such intense pressure,” Purse said.
He advises those who receive unexpected emails that use scare tactics, or ask to download or open unusual files, to treat them as a scam and not click. Search the supposed law firm or organization’s office directly and contact them directly using information on their official webpage or app.
“Nine out of 10 times, you won’t find a legitimate office or phone number, and if you do, they may not have any idea what you are talking about — then you know you are being scammed,” Purse added.